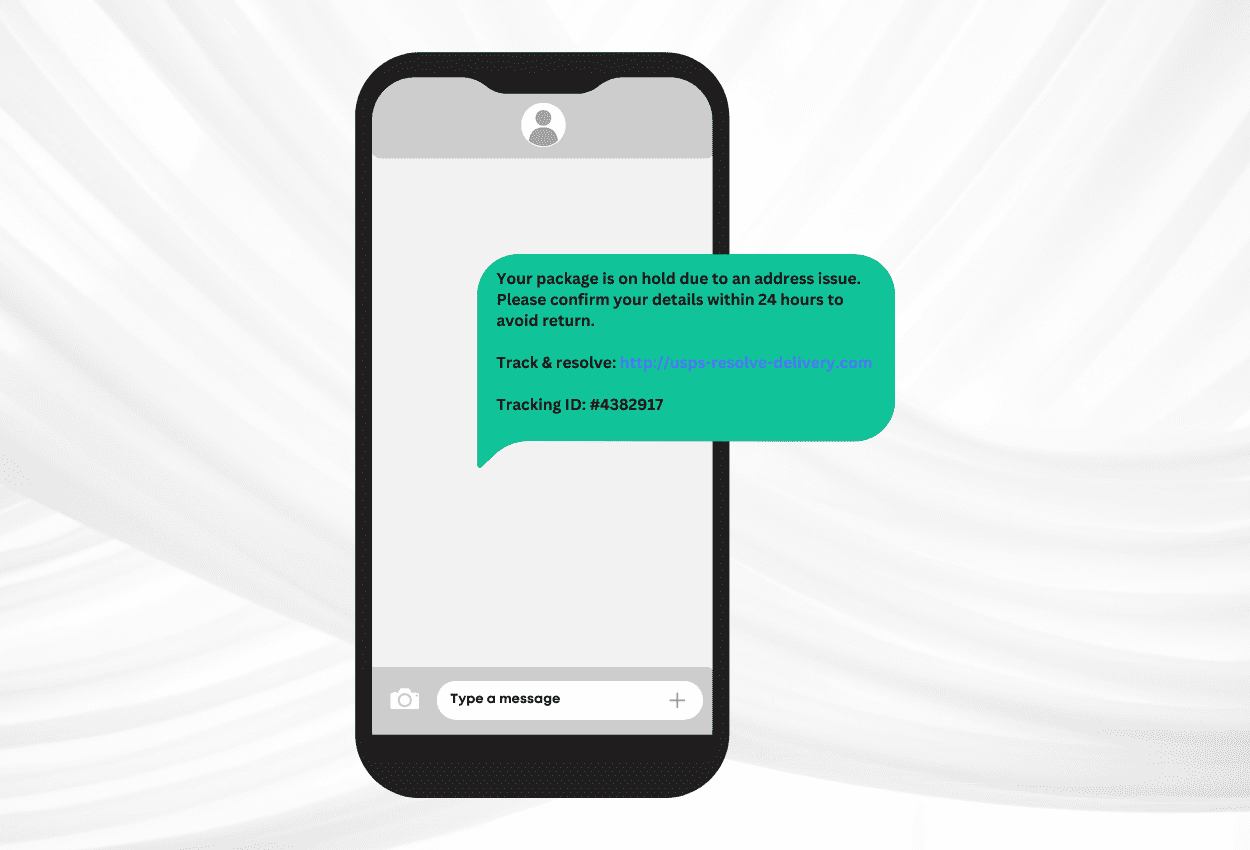
Evil-Twin attacks are when cybercriminals trick users into connecting to a real-looking public WiFi network. You may think the Free.Coffee.WiFi was legit, only to realize later that your personal information was stolen because you were on a malicious network. Once connected to these networks, the attacker can access all network traffic. They can steal information such as login credentials, financial data, messages, personally identifiable information (PII), and more. Today, we’ll be going more in-depth into the threat of an evil twin WiFi attack by discussing how it works, why it’s dangerous, and how to protect yourself.

How Evil Twin Attacks Work
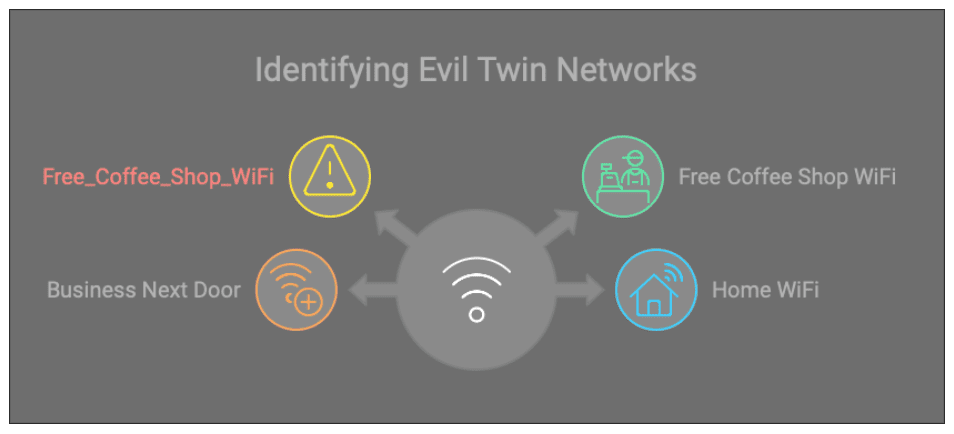
An attacker will generally set up a fake WiFi network by creating a malicious hotspot that mimics legitimate networks. If you’re at a coffee shop, their WiFi may be “CoffeeShopWifi.” An attacker may make their fake network something like “Coffee_Shop_Wifi.” Now they will use this network to intercept internet traffic. Known as a man-in-the-middle (MITM) attack, they monitor and steal data as it flows between the victim and the network.
Most of the time the attacker will broadcast a stronger signal so that devices automatically connect to the strongest WiFi, tricking users into connecting to their malicious networks. Lastly, cybercriminals usually disconnect or shut down their malicious network making it harder for a user to suspect suspicious activity.
Why Evil Twin Attacks Are Dangerous
These attacks are very dangerous, considering the amount of information one can get. These attacks exploit human trust and convenience since around 38% of people use public networks every single day. Here’s why these attacks are such a big threat:
- Data Theft: These attacks can gather any information the victim does while connected to the network. They can collect all login credentials, emails and messages, bank details, and even access corporate accounts.
- Account Compromise: Hackers can steal session cookies, letting them hijack active accounts with the need to input passwords. This can lead to unauthorized use of any accounts the victim may have been using.
- Malware Injection: Attackers can even go as far as injecting malware or ransomware on devices. This can be done through pop-up ads or them directly installing it onto the victim’s device.
- Difficulty Detecting the Attack: These attacks are very hard to detect as the malicious network usually looks very similar to the real one. When they’re done, they can take the network offline so it looked like it was never there in the first place.
How to Protect Yourself from These Attacks
Although these attacks can be hard to detect, with the proper precautions you can minimize the threat of ever falling for it. Some key ways to avoid these attacks are to:
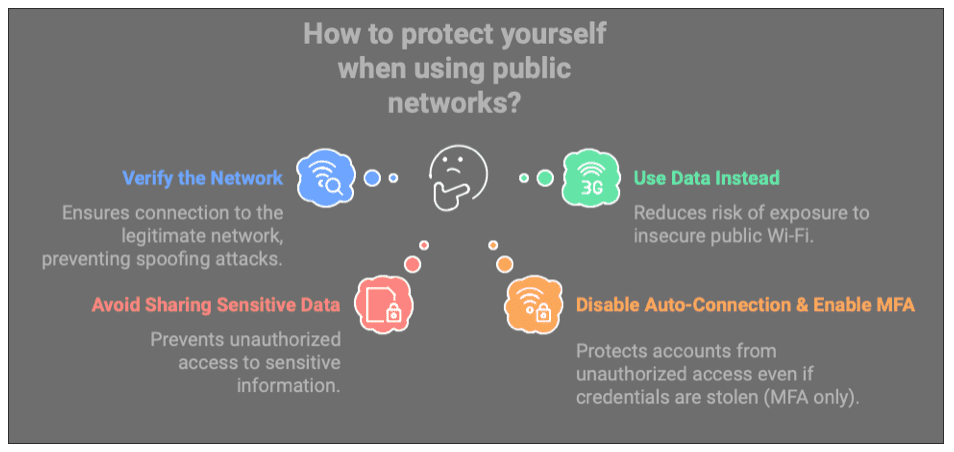
- Verify the Network: Always confirm the name of the network with whoever may have that knowledge, the barista at a coffee shop or the receptionist at a hotel. If you notice any small differences between two similar networks, always verify the legitimate one.
- Use Data Instead: Sometimes using just cellular data may be the right move when deciding if you should use public WiFi. If you’re unsure of the credibility and you may have to access sensitive information, using cellular data is a good alternative.
- Avoid Sharing Sensitive Data on Public Networks: In general, it’s a good rule of thumb is to not access sensitive data on public networks. If you must, using a VPN or encrypted websites (HTTPS) can lower the threat chances.
- Disabling Auto-Connection and Enabling MFA on Accounts: Usually, your phone will try to auto-connect to the strongest public network, disabling this is a good way to stop a potential attack. Enabling MFA on all your accounts ensures that even if your credentials are stolen, the attackers can access your data.
What We Can Learn from Evil Twin WiFi Attacks
Evil twin attacks are very simple to fall for but extremely dangerous. Taking proactive and careful measures is essential to keeping your data safe. We explained how these attacks work, why they are dangerous, and ways you can avoid being a victim of them. Of course, sometimes, even the best solutions don’t work. That’s why we at Kirkham IronTech are here, our team of experts specializes in helping businesses with their cybersecurity needs. We help businesses stay secure with active monitoring and our IronTech Framework to prevent cyber threats before they can strike.
Ready to strengthen your defenses, give us a call!
Call Us: (479) 434-1400 – Get in touch with our team.
Visit Our Website: www.kirkhamirontech.com – Learn more about our services.
Email Us: info@kirkhamirontech.com – Let us know how we can help your business.

 Tom Kirkham brings more than three decades of software design, network administration, and cybersecurity knowledge to organizations around the country. During his career, Tom has received multiple software design awards and founded other acclaimed technology businesses.
Tom Kirkham brings more than three decades of software design, network administration, and cybersecurity knowledge to organizations around the country. During his career, Tom has received multiple software design awards and founded other acclaimed technology businesses.